BMW Car Dealerships Across North America Struggle
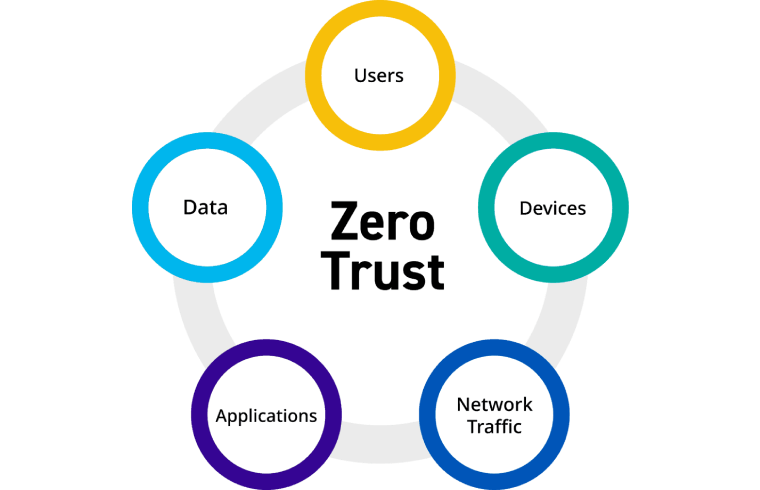
Car Dealerships Across North America Struggle with Continued Disruptions Following Cyber Attack In the wake of a significant cyber attack on BMW, car dealerships across North America are grappling with ongoing disruptions. The attack, which targeted BMW’s IT infrastructure, has had a ripple effect on the entire dealership network, leading to substantial operational challenges and […]
BMW Car Dealerships Across North America Struggle Read More »